Explain Different Fields of Udp Datagram
UDP stands for User Datagram Protocol. A datagram is a basic transfer unit associated with a packet-switched network.

Udp Overview Udp Explained Computer Networks Iit Lecture Series Youtube
UDP Checksum Integrity checking is optional under UDP.

. Port number 0 is reserved. Some port numbers can be used by both UDP and TCP1. In computer networking the UDP stands for User Datagram Protocol.
There is no relationship between the different user datagrams even if they are coming from the same source and going to the same destination source. It provides a best-effort datagram service to an End System IP host. The User Datagram Protocol has a minimalistic structure and missing.
With TCP on the other hand the header can vary from 20 to 60 bytes. It is 16 bits long which means that the port number can range from 0 to 65535. One other important protocol in the TCPIP site is User Datagram Protocol UDP.
A UDP datagram consists of a datagram header and a data section. In UDP the receiver does not generate an. The User Datagram Protocol has a minimalistic structure and missing.
The first 8 bytes of a datagram contain necessary header information and the remaining part consists of data. This is the port number used by the process running on the source host. User Datagram Protocol UDP is a protocol at Transport Layer which is not reliable when compared with Transmission Control Protocol TCPUser Datagram Protocol UDP is also called as a connection less protocol.
User Datagram Protocol UDP is a communications protocol that is primarily used to establish low-latency and loss-tolerating connections between applications on the internet. User Datagram Protocol UDP is part of the Internet Protocol suite used by programs running on different computers on a network. Some features of UDP are as stated below.
UDP provides a connectionless service. It is not delivered to the wrong protocol. The value of the protocol field for UDP is 17.
The UDP protocol allows the computer applications to send the messages in the form of datagrams from one machine to another. It is defined by RFC 768 written by John Postel. Table 41 shows some well-known port numbers used by UDP.
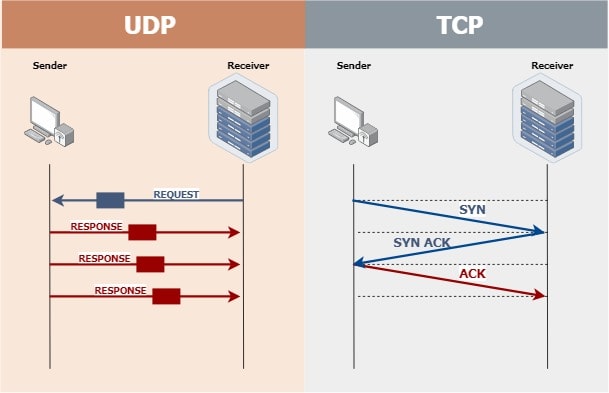
Figure2shows the format of a user datagram. Just like TCP this protocol provides delivery of data between applications running on hosts on a TCPIP network but unlike TCP it does not sequence the data and does not care about the. UDP speeds up transmissions by enabling the transfer of data before an agreement is provided by the receiving party.
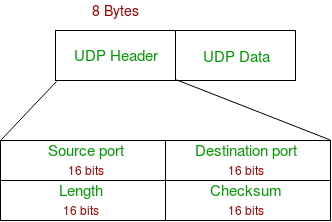
UDP Header consists of 4 fields. The header consists of a 16-bit source port a 16-bit destination port a. UDP Header Format is shown.
Figure 49 shows the format of a user datagram. And User Datagram Protocol UDP are two methods used to manage data flow through ports on a DTE device with TCP being the more complex and robust of the two. The fields for UDP port numbers are 16 bits long giving them a range that goes from 0 up to 65535.
This protocol is basically a scaled-down version of TCP. Well explain how a UDP flood attack works and provide you with an overview. At this point it is important to.
UDP port number fields are each 16-bits or 2-bytes long. Datagrams are typically structured in header and payload sections. Encapsulation and De.
The UDP datagram header consists of 4 fields each of which is 2 bytes 16 bits. UDP is used to send short messages called datagrams but overall it is an unreliable connectionless protocol. User Datagram Protocol UDP is more efficient in terms of both latency and bandwidth.
UDP has a simpler and shorter 8-byte header shown in Figure 59 compared to TCPs default header size of 20 bytesUDP header fields include source port destination port packet length header and data. The fields are as follows. The use of the checksum and source port fields is optional in IPv4 pink background in table.
UDP Checksum calculation is not mandatory. UDP packets called user datagrams have a fixed-size header of 8 bytes. As a result UDP is beneficial in time-sensitive.
Reed developed the UDP protocol in 1980. The service provided by UDP is an unreliable service that provides no guarantees for delivery and no protection. The data section follows the header and is the payload data carried for the application.
This is the port number used by the process. User Datagram Protocol UDP refers to a protocol used for communication throughout the internet. It is informally called Send and Pray for this reason.
UDP packets called user datagrams have a fixed-size header of 8 bytes. Port numbers help to distinguish different user requests or processes. UDP is officially defined in RFC 768 and was formulated by David P.
Divided into two 32-bit blocks with four different data fields the structure is as follows. Datagrams provide a connectionless communication service across a packet-switched network. Port numbers help to distinguish different.
The User Datagram Protocol UDP is simplest Transport Layer communication protocol available of the TCPIP protocol suite. It is defined in RFC 768 and it is a part of the TCPIP protocol so it is a standard protocol over the internet. Even servers for major organisations have collapsed under the massive amounts of data.
UDP is said to be an unreliable transport protocol but it uses IP services which provides best effort delivery mechanism. If this value is changed during transmission the checksum calculation at the receiver will detect it and UDP drops the packet. In this lesson you will learn more about User Datagram Protocol UDP User Datagram Protocol UDP header and header fields.
The User Datagram Protocol UDP is a transport layer protocol defined for use with the IP network layer protocol. The delivery arrival time and order of arrival of datagrams need not be guaranteed by the network. The fields are as follows.
Each user datagram sent by the UDP is an independent datagram. UDP header size is 8 bytes. If turned on both ends of the communications channel use this field for data integrity checks.
1 Source port number. Well explain how a UDP flood attack works and provide you with an overview. Both TCP and UDP.
Connectionless service UDP provides connectionless service. The different operations of UDP are as follows. UDP User Datagram Format.
An analogy to help understand the role of ports is to think of multiple packages delivered to different people at a common address such as a business office. UDP port number fields are each 16 bits long therefore the range for port numbers is defined from 0 to 65535. Even servers for major organizations have collapsed under the massive amounts of data.
Source Port is a 2 Byte long. UDP is the User Datagram Protocol a simpler and faster cousin to TCPUDP has no handshake session or reliability. Length This field describes the total length of the UDP datagram including both data and header Information.
UDP packets user datagram has a fixed size header of 8 bytes. It involves minimum amount of communication mechanism. Divided into two 32-bit blocks with four different data fields the structure is as follows.
UDP Header It is an 8-bytes fixed header. Destination Port This is the port number pertaining to the destination application. Source port number.

Comments
Post a Comment